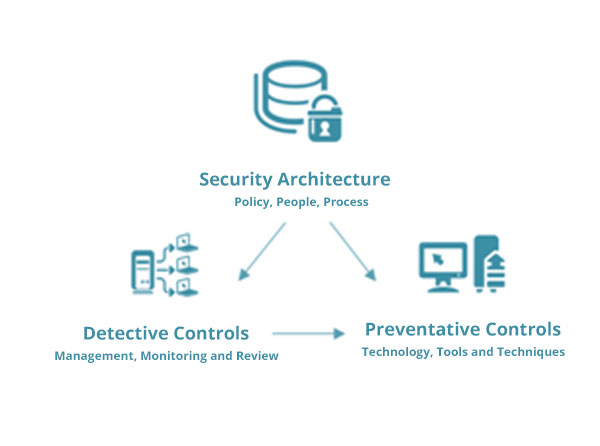
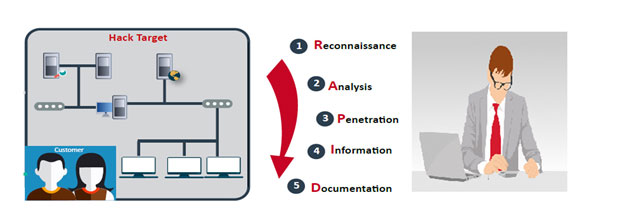
The security implementation will be carried out by Consultants and Engineers who have extensive knowledge in the selected product.
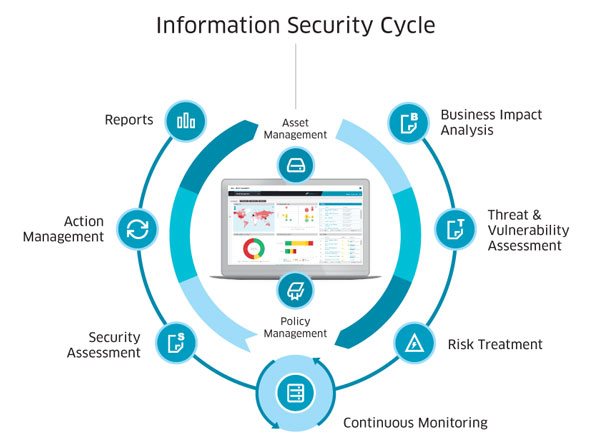
The configuration of the security design and implementation will be strictly based on the vulnerabilities, risks, and security policies identified during the Risk Assessment and Risk Treatment plan.
RSnet will then carry out assessment quarterly or upon changes in your organization to ensure:
- The security controls are fine-tuned and work in according to business and function requirements.
- The designed security architecture can withstand the latest attacks or threats.
- The security implementations are well maintained and up-to-dated.